记录:openEuler24.03升级openSSH10.0p2
openssh升级
·
记录:openEuler24.03Sp2升级openSSH10.0p2.升级需谨慎,仅供参考,欢迎交流。
1.查看openssh版本
当前版本是openssh_9.6p1,openSSL3.0,需要将openssh升级到openssh-10.0p2。
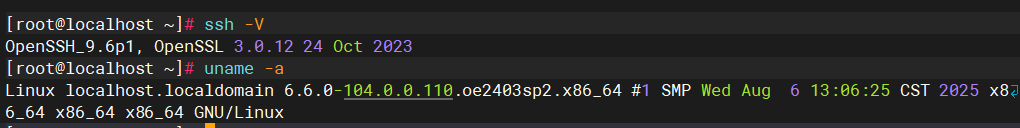
2.卸载openssh
注意原sshd配置文件,自行保存。
[[ -f /etc/ssh/sshd_config ]] && mv /etc/ssh/sshd_config /etc/ssh/sshd_config.$(date +%Y%m%d)[root@localhost ~]# rpm -qa | grep openssh
openssh-9.6p1-6.oe2403sp2.x86_64
openssh-server-9.6p1-6.oe2403sp2.x86_64
openssh-clients-9.6p1-6.oe2403sp2.x86_64
卸载openssh
for i in $(rpm -qa | grep openssh);do rpm -e $i --nodeps;done3.安装
step1:安装依赖
yum -y install gcc pam-devel zlib-devel openssl-devel tar make net-toolsstep2:下载openssh-10.0p2.tar.gz
wget https://mirrors.aliyun.com/pub/OpenBSD/OpenSSH/portable/openssh-10.0p2.tar.gzstep3:安装
#解压安装包
tar -zxvf openssh-10.0p2.tar.gz
#进入安装目录
cd openssh-10.0p1
#使用默认设置
./configure
#编译并安装
make && make install 4.配置sshd
step1:创建sshd.service服务:
进入系统服务器目录
cd /usr/lib/systemd/system
创建服务文件
vim sshd.service/usr/lib/systemd/system/sshd.service文件内容如下:
[Unit]
Description=OpenSSH server daemon
Documentation=man:sshd(8) man:sshd_config(5)
After=network.target sshd-keygen.target
Wants=sshd-keygen.target
[Service]
Type=notify
EnvironmentFile=-/etc/sysconfig/sshd
ExecStart=/usr/local/sbin/sshd -D $OPTIONS
ExecReload=/bin/kill -HUP $MAINPID
KillMode=process
Restart=on-failure
RestartSec=42s
[Install]
WantedBy=multi-user.targetstep2:修改sshd.config文件
vim /usr/local/etc/sshd_config主要修改内容:
- PermitRootLogin yes
PasswordAuthentication yes - 原sshd配置内容,例如sftp等
升级前有sftp服务,升级后无法使用,所以我这里内容如下:添加了一个端口为1012的sftp服务,将Subsystem sftp /usr/libexec/openssh/sftp-server #这一行注释掉,并添加sftp信息。
# $OpenBSD: sshd_config,v 1.105 2024/12/03 14:12:47 dtucker Exp $
# This is the sshd server system-wide configuration file. See
# sshd_config(5) for more information.
# This sshd was compiled with PATH=/usr/bin:/bin:/usr/sbin:/sbin:/usr/local/bin
# The strategy used for options in the default sshd_config shipped with
# OpenSSH is to specify options with their default value where
# possible, but leave them commented. Uncommented options override the
# default value.
Port 22
Port 1012
#AddressFamily any
ListenAddress 0.0.0.0:22
ListenAddress 0.0.0.0:1012
#ListenAddress ::
#HostKey /usr/local/etc/ssh_host_rsa_key
#HostKey /usr/local/etc/ssh_host_ecdsa_key
#HostKey /usr/local/etc/ssh_host_ed25519_key
# Ciphers and keying
#RekeyLimit default none
# Logging
#SyslogFacility AUTH
#LogLevel INFO
# Authentication:
#LoginGraceTime 2m
#PermitRootLogin prohibit-password
PermitRootLogin yes
#StrictModes yes
#MaxAuthTries 6
#MaxSessions 10
#PubkeyAuthentication yes
# The default is to check both .ssh/authorized_keys and .ssh/authorized_keys2
# but this is overridden so installations will only check .ssh/authorized_keys
AuthorizedKeysFile .ssh/authorized_keys
#AuthorizedPrincipalsFile none
#AuthorizedKeysCommand none
#AuthorizedKeysCommandUser nobody
# For this to work you will also need host keys in /usr/local/etc/ssh_known_hosts
#HostbasedAuthentication no
# Change to yes if you don't trust ~/.ssh/known_hosts for
# HostbasedAuthentication
#IgnoreUserKnownHosts no
# Don't read the user's ~/.rhosts and ~/.shosts files
#IgnoreRhosts yes
# To disable tunneled clear text passwords, change to "no" here!
PasswordAuthentication yes
#PermitEmptyPasswords no
# Change to "no" to disable keyboard-interactive authentication. Depending on
# the system's configuration, this may involve passwords, challenge-response,
# one-time passwords or some combination of these and other methods.
#KbdInteractiveAuthentication yes
# Kerberos options
#KerberosAuthentication no
#KerberosOrLocalPasswd yes
#KerberosTicketCleanup yes
#KerberosGetAFSToken no
# GSSAPI options
#GSSAPIAuthentication no
#GSSAPICleanupCredentials yes
# Set this to 'yes' to enable PAM authentication, account processing,
# and session processing. If this is enabled, PAM authentication will
# be allowed through the KbdInteractiveAuthentication and
# PasswordAuthentication. Depending on your PAM configuration,
# PAM authentication via KbdInteractiveAuthentication may bypass
# the setting of "PermitRootLogin prohibit-password".
# If you just want the PAM account and session checks to run without
# PAM authentication, then enable this but set PasswordAuthentication
# and KbdInteractiveAuthentication to 'no'.
#UsePAM no
#AllowAgentForwarding yes
#AllowTcpForwarding yes
#GatewayPorts no
#X11Forwarding no
#X11DisplayOffset 10
#X11UseLocalhost yes
#PermitTTY yes
#PrintMotd yes
#PrintLastLog yes
#TCPKeepAlive yes
#PermitUserEnvironment no
#Compression delayed
#ClientAliveInterval 0
#ClientAliveCountMax 3
#UseDNS no
#PidFile /var/run/sshd.pid
#MaxStartups 10:30:100
#PermitTunnel no
#ChrootDirectory none
#VersionAddendum none
# no default banner path
#Banner none
# override default of no subsystems
#Subsystem sftp /usr/local/libexec/sftp-server
# Example of overriding settings on a per-user basis
#Match User anoncvs
# X11Forwarding no
# AllowTcpForwarding no
# PermitTTY no
# ForceCommand cvs server
Subsystem sftp internal-sftp
Match LocalPort 1012 User zfb_sftp
ChrootDirectory %h # 锁定到用户主目录
ForceCommand internal-sftp
AllowTcpForwarding no
X11Forwarding no
PermitTTY nostep3:重启
#重新加载服务
systemctl daemon-reload
#设置开机自启动
systemctl enable sshd
#查看sshd配置是否正确
sshd -t
#重启
systemctl restart sshd最后验证ssh版本和sftp是否正常: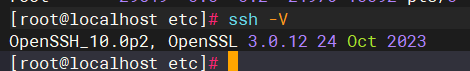
如果没有sshd生效:
查看当前sshd进程
# 检查是否有多个 sshd 进程,如果有旧的sshd服务,kill
ps aux | grep sshd
# 杀死所有 sshd 进程,注意:会断开所有sshd,谨慎操作
pkill -9 sshd
# 重新启动服务
systemctl start sshd
鲲鹏昇腾开发者社区是面向全社会开放的“联接全球计算开发者,聚合华为+生态”的社区,内容涵盖鲲鹏、昇腾资源,帮助开发者快速获取所需的知识、经验、软件、工具、算力,支撑开发者易学、好用、成功,成为核心开发者。
更多推荐
 已为社区贡献2条内容
已为社区贡献2条内容







所有评论(0)